Supermassive “Mother of All Breaches“: 26 Billion Records Leaked— And What You Can Do to Protect Yourself

Security researchers from CyberNews and Security Discovery have discovered what may now be the biggest data breach database in history to date.
What Should I Know?
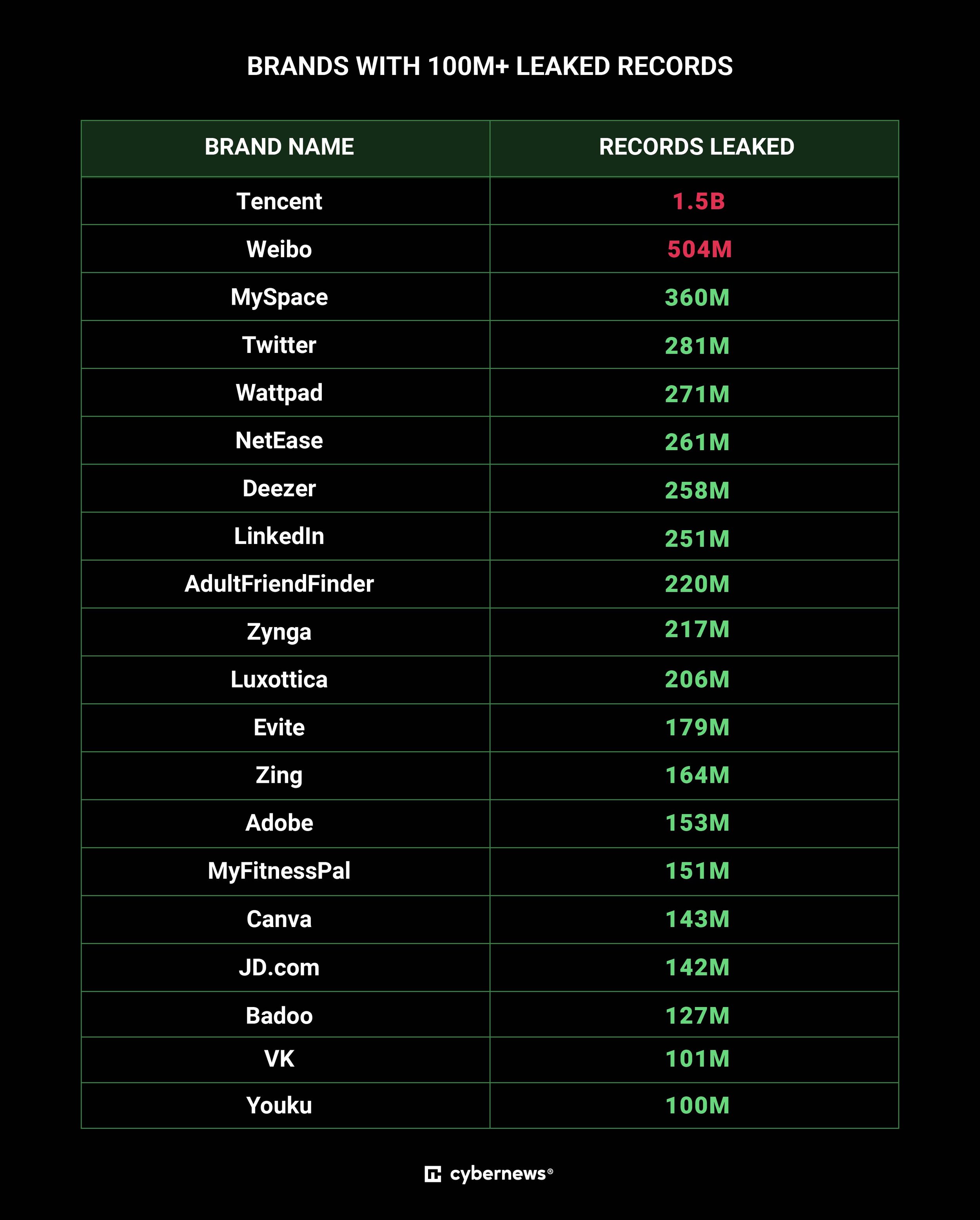
Dubbed “Mother of All Breaches” or MOAB, the mammoth database runs up to 12 terabytes in size holding 26 billion records, estimated to equal 15,600 filing cabinets of sensitive information and user credentials. For scale, previously known breaches have maxed out just over 3 billion records. Found on an open storage instance, MOAB contains over 3,800 folders of user information from platforms and services like LinkedIn, Twitter, Dropbox, Adobe, Telegram, Canva, as well as tech giant Tencent. Researchers also identified an assortment of government records from the US, Germany, Brazil, Philippines, Turkey, amongst others. The database is thought to have been compiled by a malicious actor or data broker and could be weaponized in a wide range of attacks such as identity theft, unauthorized access to sensitive or personal accounts, targeted cyberattacks and sophisticated phishing scams.
What Can I Do?
To start— don’t panic. While 26 billion is a staggering amount of records, researchers have found that many have been meticulously organized from thousands of previous breaches and there are likely even duplicates within this compilation. There are definitely new leaks that have not been found before, but there is also a lot you can do to stay ahead. Change your passwords to be strong, complex, and unique; set up multi-factor authentication where possible; and stay alert to an increase in attempted phishing emails in the coming few months. Sites such as Have I Been Pwned or the Personal Data Leak Checker allow you to check if your accounts have been compromised in any known breaches.
More than any other time, now is the best time to start.
Reach out to a trusted managed services provider like Interware to check your blind spots and strengthen your defenses. They can assess your security posture, offer training to identifying advanced phishing schemes, and set up services like a password manager, data security protection, and more.































